eLBaaS - embedded Linux Build as a Service
An AWS like "no-code" build solution for embedded OS customization to address typical software integration, deployment and maintenance issues in embedded Linux world.
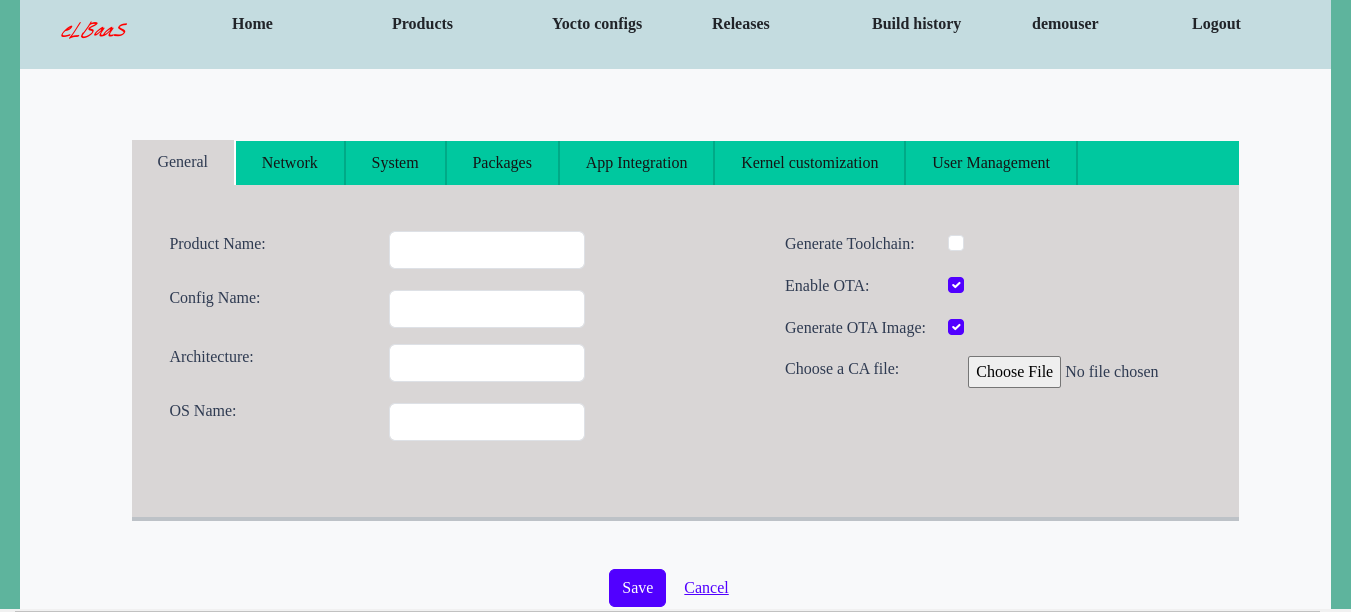
An AWS like "no-code" build solution for embedded OS customization to address typical software integration, deployment and maintenance issues in embedded Linux world.

eLBaaS is one of its kind. Built to kill the gap in embedded Linux integration, deployment and maintanance in the area of wide spreading IoT.
Rapid prototyping of embedded Linux based devices. Just pick a well known SoC (RPi) and build the OS with few clicks!
Learn MoreDeploy your device without any explicit configuration at customer site. Super helpful when you have plenty of devices to deploy!
Learn MoreWe take care of your Yocto/BSP (Board Support Package) maintanance whether it's a well known or a custom SoC. Making sure no well known security issues can hamper your product!
Learn MoreProduct owner takes control of the product. eLBaaS brings everyone of the development team togather working as a center piece for development.
Learn MoreeLBaaS (the build tool) opens up the opportunity to use already prepared YOCTO for you. eLBaaS offers a clean and easy to use web based interface for building embedded GNU/Linux distribution. Everyone in a team can organize themselves surrounding eLBaaS. eLBaaS being at the center piece of the development can help you to take important decisions along the product development life cycle. Once the product is in the market - eLBaaS maintenance can help to ensure that product is secure, bug free and up-to date with all the new software versions.
Learn More
We would love to answer your questions! Checkout the FAQ if we answered it beforehand.
Dhaka, Bangladesh (currently operating remotely) Please contact us via e-mail.
info@elbaas.dev